CS417 Exam 1
Fall 2013
Paul Krzyzanowski
- 4 points
Why is processor affinity important in a NUMA (non-uniform memory access) multiprocessor system? - 4 points
Explain how the following techniques yield improved performance.
(a) Compounding (compound RPC)
(b) Multi-canonical marshaling
(c) Client-side caching - 4 points
AFS supports long-term caching of data on the client. Explain the mechanism in the design of the file protocol to ensure that cached files are not out obsolete. - 8 points
The timeline illustrates a system of three processes P0, P1, P2 with events taking place on each of these processes. Some of the events are the sending or receiving of a message. Some of these messages are multicasts, where the sending of a message to multiple recipients is a single event.
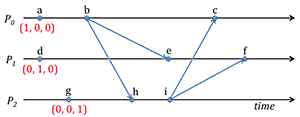
(a) Assign vector timestamps to the six remaining events.
(b) Which events are concurrent with event e? - Metcalfe's law states that:
(a) A system with n processors requires n(n-1)/2 network connections.
(b) The number of transistors on a chip doubles approximately every two years.
(c) The value of a network is proportional to the square of the number of connected users of the system.
(d) Adding a processor to a multiprocessor system of n processors will speed the system by at most (n+1)/n. - A snoopy cache is designed for:
(a) Bus-based multiprocessor systems.
(b) Crossbar connected switched multiprocessor systems.
(c) NUMA multiprocessor systems.
(d) All of the above. - A directory in a cache coherent NUMA system is used to:
(a) Provide a centralized cache for all processors in the system.
(b) Keep track of which processors have cached copies of a processor's memory.
(c) Keep track of all the processors that are participating in a computation.
(d) Provide a multi-level hierarchy to the system cache. - The Internet Protocol, IP, expects what type of underlying network?
(a) Unreliable packet switched network.
(b) Reliable packet switched network.
(c) Broadband network using frequency division multiplexing (FDM).
(d) Virtual circuit network using time division multiplexing (TDM). - A port number in some IP protocols is used at the:
(a) Network layer to uniquely identify a computer on the network.
(b) Transport layer to identify communication endpoints within a process.
(c) Session layer to separate data coming from one socket into multiple logical streams.
(d) Data link layer to send and receive packets on the underlying physical network. - TCP/IP tries to simulate a virtual circuit network but does not offer:
(a) In-order message delivery.
(b) Reliable message delivery.
(c) Connection setup.
(d) Constant latency. - Embedding an IP packet within an Ethernet packet is an example of:
(a) A network tunnel.
(b) Protocol switching.
(c) Transport layer delivery.
(d) Protocol encapsulation. - Java allows a client to create a connected TCP socket by calling the Socket constructor. This constructor performs the following system calls:
(a) socket, bind, listen
(b) socket, listen, accept
(c) socket, connect, accept
(d) socket, bind, connect - Which is not true about explicit typing in RPC marshaled data?
(a) The server can identify and convert data types of parameters if necessary.
(b) It is easier to support polymorphism (the same function name taking different data types as parameters).
(c) Functions that take optional parameters can be supported.
(d) Messages tend to be more efficient than those using implicitly typed data. - A surrogate process in Microsoft DCOM is a:
(a) Process on the server that loads a COM object on behalf of the client.
(b) Process on the server that inherits any active objects once the server processes that used them die.
(c) Client-side COM object that is a stub, using RPC to talk to a server.
(d) A process running on the client to which local processes send messages to reach the server. - Google Protocol Buffers are designed to:
(a) Serve as a memory allocation mechanism to move network messages between kernel and user space.
(b) Serialize structured data.
(c) Provide support in the operating system kernel for managing network protocol headers.
(d) Generate state machines that implement a network protocol. - Why is leasing preferred over remote reference counting for distributed garbage collection?
(a) It results in fewer network messages.
(b) The network messages are smaller.
(c) It is fault tolerant.
(d) It optimizes server resources by removing an object immediately when it is no longer needed. - A server running the Berkeley algorithm has a time of 2:00:00. Client A has a time of 2:04:00. Client B has a time of 2:05:00. What is A's clock set to when the algorithm is run?
(a) 2:00:00.
(b) 2:02:00.
(c) 2:03:00.
(d) 2:04:30. - A client sends a message to a time server at 2:00:00.000. It receives a response at 2:00:00.120 (120 ms later). The timestamp from the server contains 2:00:01.000. Using CristianÕs algorithm, to what time does the client set its clock?
(a) 2:00:00.880
(b) 2:00:00.940
(c) 2:00:01.060
(d) 2:00.01.120 - If the best case round-trip time between the client and server is 80 ms (0.080 s), what is the error in question 18?
(a) ± 20 ms
(b) ± 40 ms
(c) ± 60 ms
(d) ± 120 ms - If event A has a Lamport timestamp L(A), event B has a Lamport timestamp L(B), and L(A) < L(B), what is the strongest statement you can make about events A and B?
(a) A causally precedes B.
(b) A and B are concurrent events.
(c) If A and B are causally related, then A happened before B.
(d) A took place before B but may or may not be causally related to B. - When trying several NTP servers, a client should synchronize from the one that:
(a) Reports the smallest offset from the client's time since this will minimize the amount of adjustment.
(b) Is at a lowest stratum (that is, closest to a server connected to an accurate time source).
(c) Results in the shortest delay.
(d) Results in the smallest error, even if it is at a higher stratum (more hops from an accurate time source). - PTP, the Precision Time Protocol:
(a) Has the server initiate the sync.
(b) Ignores network delays since it is designed for high-speed local area networks (LANs).
(c) Averages the time between a client and server since there is no master time source on a LAN.
(d) Achieves great accuracy by performing three synchronizations successively. - Which message ordering can be achieved with processes attaching a monotonically increasing sequence number that is provided from a central server to their sent messages?
(a) Global
(b) Total
(c) Causal
(d) Sync-ordered - IP multicasting provides this form of ordering and reliability:
(a) Unordered, unreliable
(b) Unordered, reliable
(c) FIFO ordered, reliable
(d) FIFO ordered, unreliable - PIM (Protocol Independent Multicast) Sparse Mode multicast:
(a) Is designed only for Local Area Networks (LANs).
(b) Directs all multicast traffic to a common point in the network.
(c) Builds a spanning tree that covers the entire network originating with the multicast transmitter.
(d) Ensures an optimum route between the multicast sender and receiver. - Which file system was designed with client-side file consistency and behavior close to local files as top priorities?
(a) NFS
(b) AFS
(c) CODA
(d) SMB - Initial versions of NFS used RPC over UDP but not because:
(a) UDP is more reliable.
(b) There is no need to reestablish connections after an intermittent network loss.
(c) UDP uses fewer server resources than TCP.
(d) UDP is faster. - Microsoft opportunistic locks (oplocks):
(a) Let clients cache information without worrying about changes to the file at the server.
(b) Allow a client to lock a region of a remote file so other clients cannot access it.
(c) Ensure that only one client is granted access to a file at a time.
(d) Provide a transaction log to allow recovery after a network failure - CODA does not support:
(a) Token-based file access.
(b) Session semantics.
(c) Replicated servers.
(d) Disconnected operation. - SMB2's credit-based flow control:
(a) Gives the server control of how many messages it is willing to receive from each client.
(b) Ensures an equal balance of messages from the client to the server and from the server to the client.
(c) Gives each client control of the rate of messages it is willing to receive from connected servers.
(d) Provides a mechanism to bill clients for the amount of server resources they use.
Part I – 28 points
Part II – 55 points – 3 points each
For each statement, select the most appropriate answer. You may omit one question. Please indicate your choice clearly.